When the “what-if” becomes “what’s next” – Why the alleged GCash leak matters to every Filipino
Allegations have surfaced that millions of GCash user records - including eKYC data, ID scans, and linked accounts - are being sold on a dark-web forum.
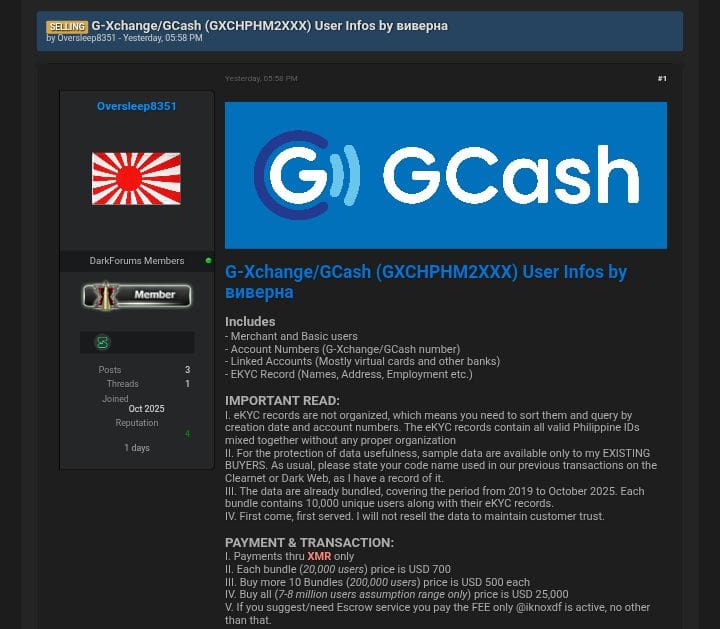
On 25 October 2025, a listing surfaced on a dark‐web forum by a seller using the handle “Oversleep8351” claiming to offer for sale a massive dataset belonging to G‑Xchange, Inc. (operator of GCash) — allegedly covering “merchant and basic GCash users … linked accounts … eKYC records such as names, addresses, employment details” and scans of Philippine identification documents. Deep Web Konek
Although the authenticity of the listing has not been definitively verified by regulators, the consequences if this turns out to be true are significant — for individuals, for the financial technology ecosystem in the Philippines, and for regulatory and risk management frameworks. As someone who lives and works in the networking and infrastructure space, I believe it merits careful examination.
1. The individual risk profile escalates drastically
Here are some of the direct consequences for users if the data is legitimate:
- Identity theft and impersonation. When eKYC records, scans of IDs, addresses and employment details are exposed, malicious actors may assume identities at scale — opening bank or e-wallet accounts, applying for credit, or committing fraud using your data.
- SIM-swap, OTP interception and account takeover. The dataset reportedly includes mobile numbers, “linked accounts” and virtual cards (via the listing). That gives attackers a very good starting point for hijacking your phone number or intercepting OTPs to gain control of digital accounts. Brinztech - Cyber Guardian
- Phishing and targeted social engineering. With detailed personal data, attackers can craft very convincing messages or impersonation attempts. The more information they have about you, the more plausible the fraud becomes.
- Long-tail risk: you may not see it immediately. Many breaches go undiscovered for months or years; even if your funds are safe now, exposure of your personal information remains a ticking risk.
As a user of digital financial services, the principle is simple: assume the data may already be out, and harden your defences accordingly.
2. For fintech / e-wallet providers and the broader ecosystem – trust is fragile
If the listing is genuine, the stakes for GCash (and similar providers) extend far beyond one incident:
- Erosion of user trust. A breach of eKYC data shakes foundational trust in a service that handles both personal identity and money. Users may shift to alternatives or become less willing to use digital financial services.
- Regulatory and legal exposure. In the Philippines the National Privacy Commission (NPC) oversees the Data Privacy Act of 2012; the Cybercrime Investigation and Coordinating Center (CICC) may also be involved. Previously the CICC indicated the listing did not conform with naming protocols and found “no story” yet. BusinessWorld Online If validated, the company may face regulatory inquiry, remediation requirements, and reputational costs.
- Operational risk escalation. When a large-scale dataset is allegedly sold in bundles (the listing said 10,000-user bundles at USD 700, full database for USD 25,000) Deep Web Konek it suggests either internal access or large-scale compromise — which means internal controls, vendor risk, system architecture, and incident response need urgent review.
- Systemic risk to digital finance adoption. If a top e-wallet service is compromised, it can raise questions about the security of digital financial infrastructure in the country, slowing adoption or triggering regulatory tightening which may raise costs for all providers.
3. Hidden vulnerabilities exposed – infrastructure, processes, supply chain
From a technical and operational standpoint, some of the deeper implications:
- Data at-rest and encryption. How was such sensitive data stored? If raw ID scans and eKYC records are held in accessible form, encryption, access controls and segregation may be insufficient.
- Vendor/third-party risk. Often data leaks occur via third-party services or subprocessors. A leak of this scale may indicate inadequate vetting or monitoring of partners.
- Logging, naming protocols and forensic readiness. According to CICC commentary, the alleged files didn’t match naming protocols so their origin was unclear. BusinessWorld Online That suggests forensic trails may be weak, making investigation — and therefore improvement — harder.
- Detection and response latency. A database listed on the dark web implies the attacker expected monetisation. If no breach alert, notification, or mitigation had happened yet, then the incident-response capability is under pressure.
- Persistence of personal data risk. Unlike credit card numbers that can be changed, ID scans, names, addresses and employment history do not easily change. Once exposed they represent enduring exposure.
- Interdependency of platforms. If GCash accounts are “linked accounts” including virtual cards and bank connections, then a leak is not purely about one service but touches interlinked systems — increasing the potential blast radius.
4. What should users do now – practical steps
As a technical director and someone used to designing infrastructure, here are practical, immediate steps I’d recommend for users (and organisations) to treat this as assumed real until proven otherwise:
For Users (individuals):
- Enable and enforce multi-factor authentication (MFA) everywhere (for your e-wallets, banking, email).
- Treat your mobile number as a sensitive piece of data: consider using a separate number for financial services or a second SIM/number if feasible.
- Monitor your credit reports (if available in the Philippines) and transaction history closely.
- Beware of phishing campaigns: expect that attackers may now have your full name, address, ID type, employer — making spear-phishing much easier.
- Limit the amount of funds kept in “hot” digital wallets; use regular audits of connections and linked accounts.
- Consider placing alerts on your accounts with your bank or e-wallet provider for large transactions, new device logins, or unusual behaviour.
For Organisations (fintech, e-wallets, data handlers):
- Treat this alleged listing as a serious red-flag: start or refresh your incident response, forensic review, root-cause investigation and audit of access/logging protocols.
- Review your data classification: identify which data is “critical identity data” and ensure higher protection (encryption at rest, minimal access, strong logging).
- Re-evaluate third-party risk: ensure all subprocessors/vendors are actively monitored and contractually obligated to strong security controls.
- Communicate transparently with users and regulators: even before full verification, providing timely update can preserve trust.
- Run continuous monitoring for credential stuffing, account takeover attempts, and anomalies — especially given the magnitude of the alleged exposure (millions of users).
- Consider offering identity-protection services or remediation support to users potentially impacted, as part of risk mitigation and brand protection.
5. Why this matters beyond one company – infrastructure for our digital future
The significance of this event (if confirmed) extends to national digital-finance strategy and infrastructure:
- The Philippines is actively transitioning toward “cashless” and “digital first” platforms. A large-scale exposure of one of the biggest e-wallets diminishes confidence in that transition.
- Trust is a pillar of digital ecosystems: if mass personal data is perceived to be insecure, adoption slows, cost of compliance rises, and innovation may be slower.
- Regulatory regimes will likely respond — meaning more stringent requirements for fintech and e-wallet providers, more audits, more oversight. From a cost and operational perspective this will matter.
- This is an opportunity for all service providers (including network, infrastructure, routing, edge deployments) to revisit their own “data pipeline” security: how personal data flows from app → verification services → storage → archival. In my world of network operations and NOC services this serves as a reminder that the “last mile” and “backend checking” matter nearly as much as the “front-end” user experience.
- The cross-sector ripple is significant: payment systems, banking, telecommunications (SIM swaps), identity verification services all must check their dependencies and prepare for elevated threat posture.
6. Final thoughts – pragmatic next steps for leadership (board/CTO)
If I were advising a fintech leadership team (or a board) today, here are priority action items:
- Convene an incident triage team now (or confirm the existing team) to validate whether or not the alleged dataset is real, what portion of the business/data is impacted, and the potential exposure timeline.
- Engage independent forensic specialists to verify the leak-claim, perform dark-web scanning for the dataset, and estimate how many records may be legitimately exposed.
- Develop and publish a transparent user communication plan: acknowledging the issue, stating what you know, what you’re doing, and how you protect users. Silence signals risk.
- Review and refresh vendor/subprocessor contracts, SLAs, security audits, and vendor-risk monitoring.
- Raise the bar on “data minimalism”: what identity data do you need to collect, how long do you need to keep it, how securely is it stored, how frequently is it accessed?
- Scenario-plan for regulatory enforcement, reputational impact, user-compensation costs, and cyber-insurance implications.
- Upgrade monitoring and threat-detection capabilities: this is not a “one-time” fix; attackers will exploit this dataset for years via account-takeovers, impersonation, credential reuse.
- Consider identity-protection or credit-protection services for impacted users as part of remediation strategy. It may cost now, but builds trust.
Conclusion
We may not yet know whether the listing for the GCash dataset is fully verified. The regulator commentary thus far has been cautious, indicating no confirmed breach inside the company’s systems. Inquirer.net But in my view — given the scale and detail of the claim (millions of records, spanning years, eKYC images, ID scans) — it is prudent to operate as if the dataset is compromised and prepare accordingly.
For individual users: act now. Use strong authentication, monitor accounts, assume your information may be in the wild and harden accordingly.
For providers and infrastructure stakeholders (including those of us in networking, routing, data-handling, operations): treat this as a high-risk event. It’s a reminder that the weakest link often lies not at the user interface but deep in the data pipelines, vendor processes, logging, and forensic readiness.
For the Philippine digital-economy as a whole: trust, security, transparency will determine momentum. Incidents like this — if real — test the resilience of the ecosystem and demand leadership attention.


![[Mashable] Discord.io suffers massive data breach, announces closure](https://images.unsplash.com/photo-1614680376739-414d95ff43df?crop=entropy&cs=tinysrgb&fit=max&fm=jpg&ixid=M3wxMTc3M3wwfDF8c2VhcmNofDF8fGRpc2NvcmR8ZW58MHx8fHwxNjkyNzYwMTg4fDA&ixlib=rb-4.0.3&q=80&w=960)
![[SecurityWeek] Swiss Fear Government Data Stolen in Cyberattack](https://images.unsplash.com/photo-1624969862644-791f3dc98927?crop=entropy&cs=tinysrgb&fit=max&fm=jpg&ixid=M3wxMTc3M3wwfDF8c2VhcmNofDJ8fHRoaWVmfGVufDB8fHx8MTY4NjYwMTQ5OXww&ixlib=rb-4.0.3&q=80&w=960)
